Information Gathering with Shodan
Today a large number of devices are connected to Internet, from smartphones or watches to air-conditioning devices or even refrigerators: this is what has been called “Internet of Things” (IoT), i.e. the network composed by physical devices collecting and exchanging data between themselves.
Of course, a wrong configuration of these devices can generate serious problems in terms of privacy.
The simplest example is given by private webcams, or better what they are intended to be: in fact, if they are set to have a public IP address and have not been secured properly, they can be accessed from anywhere in the world by anyone.
Moreover, even if configured to request login credentials, many of them still have default access values, which can be easily acquired by reading user manual.
Generally, depending from the webcam model, the web control interface has a default page title and a defined pattern in the url used for browser access (the only difference will be the IP address). So, once we know the title or the url pattern for a specific model, we can generate a Google query to search all the devices of that type exposed on the Internet with the same technique used in the previous article.
An example is given by this simple query which exploits the web console interface title:
intitle:"Live View / - AXIS"
In this way we can find all webcams from AXIS manufacturer with a public IP address indexed by Google.
However, there is a really powerful search engine for the IoT called Shodan that makes all the hard work for us: https://www.shodan.io
The search engine for the Internet of Things
The description in the website says that Shodan is the world’s first search engine for Internet-connected devices:
Here it is possible to look for industrial control systems, databases, video games servers, routers, webcams, refrigerators and so on; in fact, mainly using banner grabbing technique by interrogating ports, Shodan is able to discover a lot of informations about publicly exposed devices. This is the big difference between Google and Shodan: while the first one crawls for data on web pages, the latter probes for ports and captures resulting banners.
We can either use directly the search form or use the Explore button for a guided search through the available categories using predefined queries. I highly suggest to register to the site in order to gain access to features like filters and reports (including the API key).
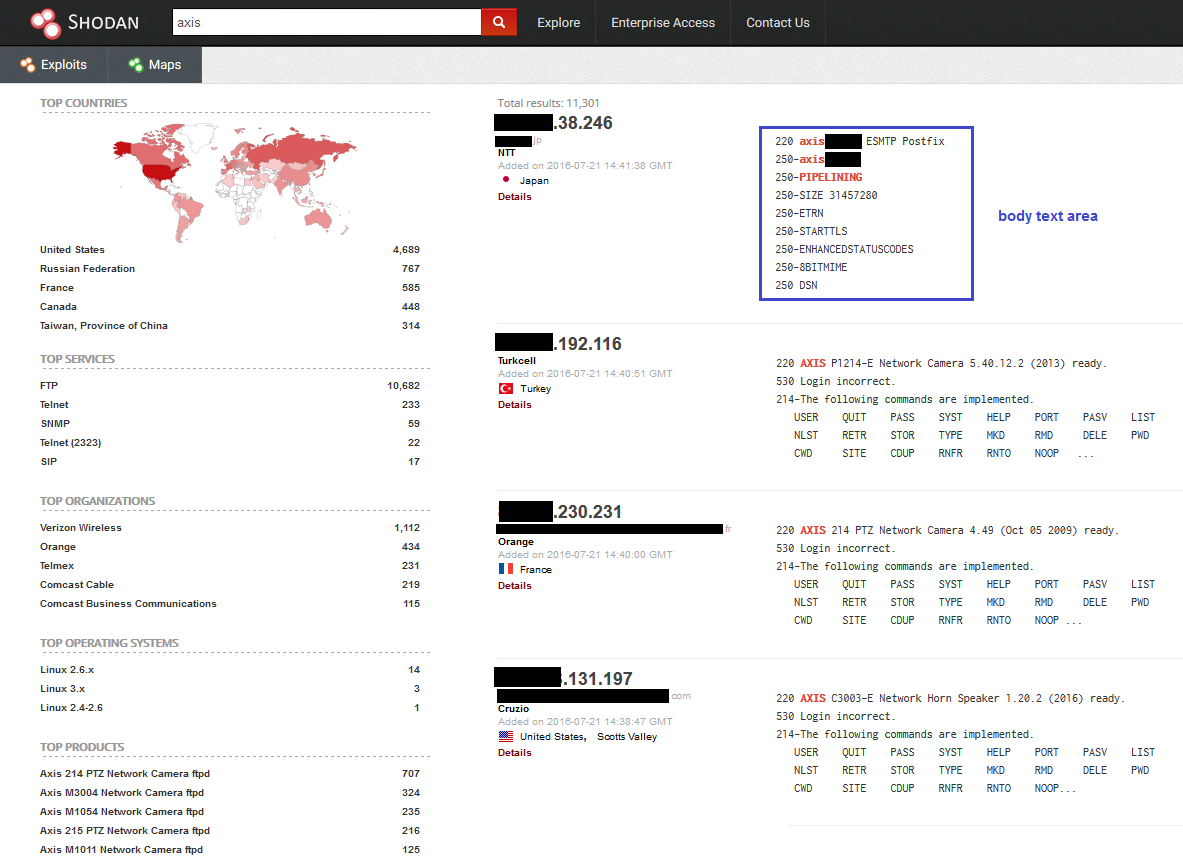
Suppose we want to search for AXIS devices, we compile the search form and launch the query:
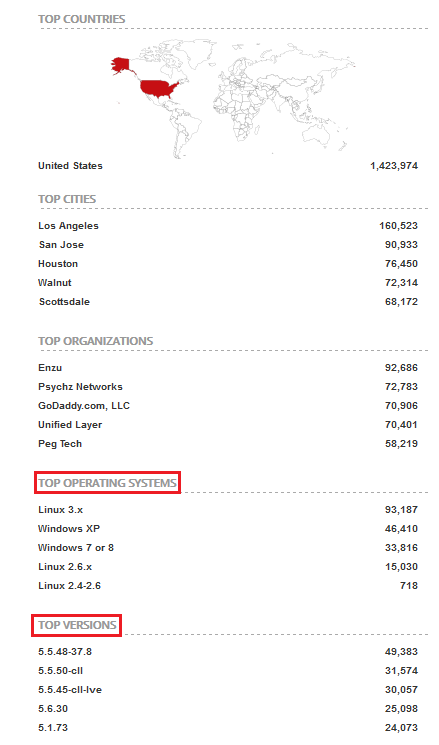
The above image shows the results page; on the left side of the screen we have five interesting groups (they change depending on the query):
- Top countries;
- Top services;
- Top organizations;
- Top operating systems;
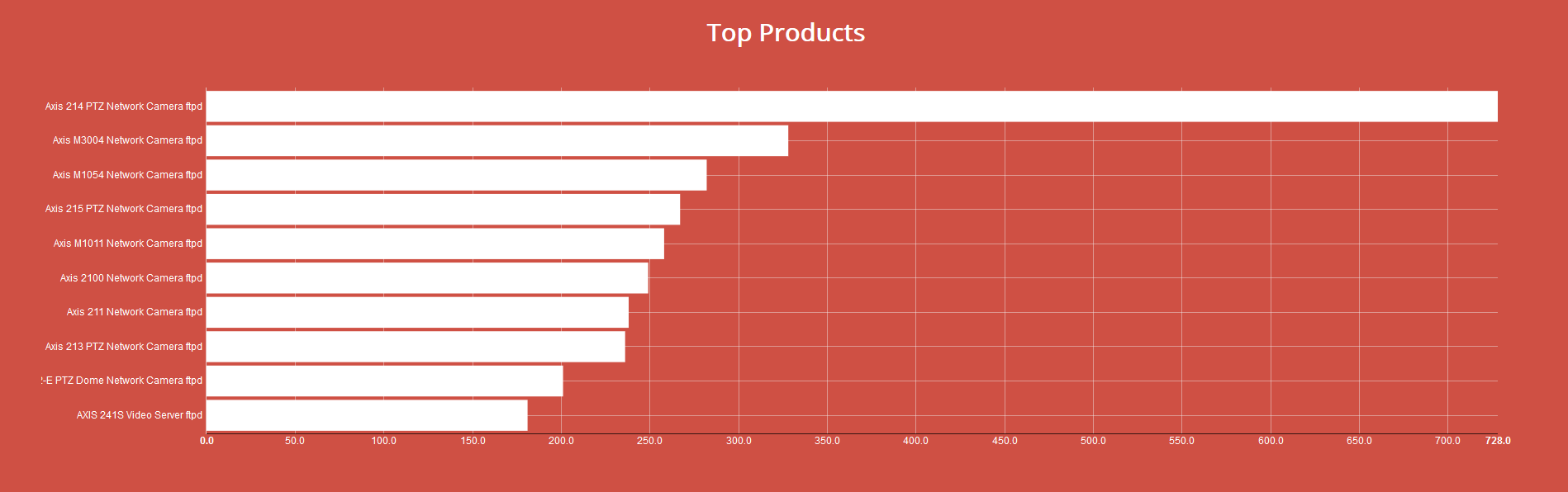
- Top products.
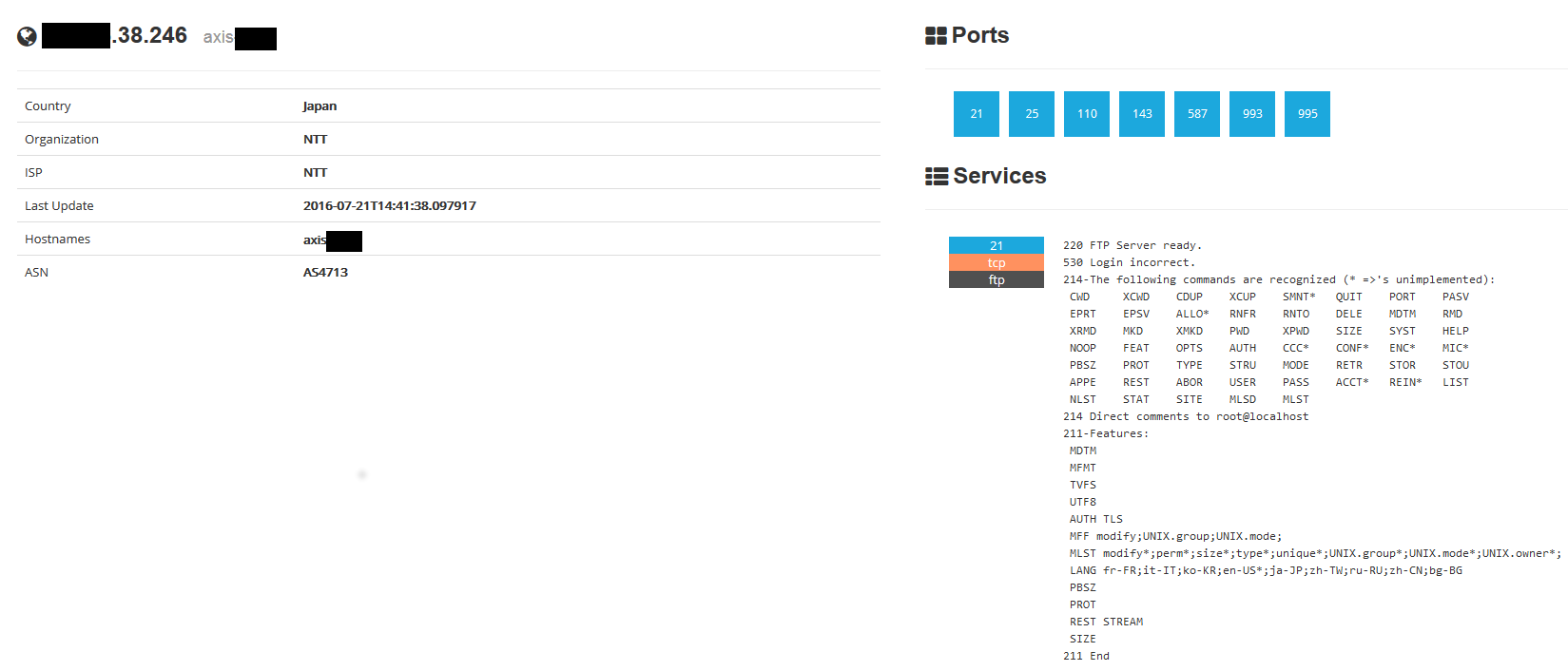
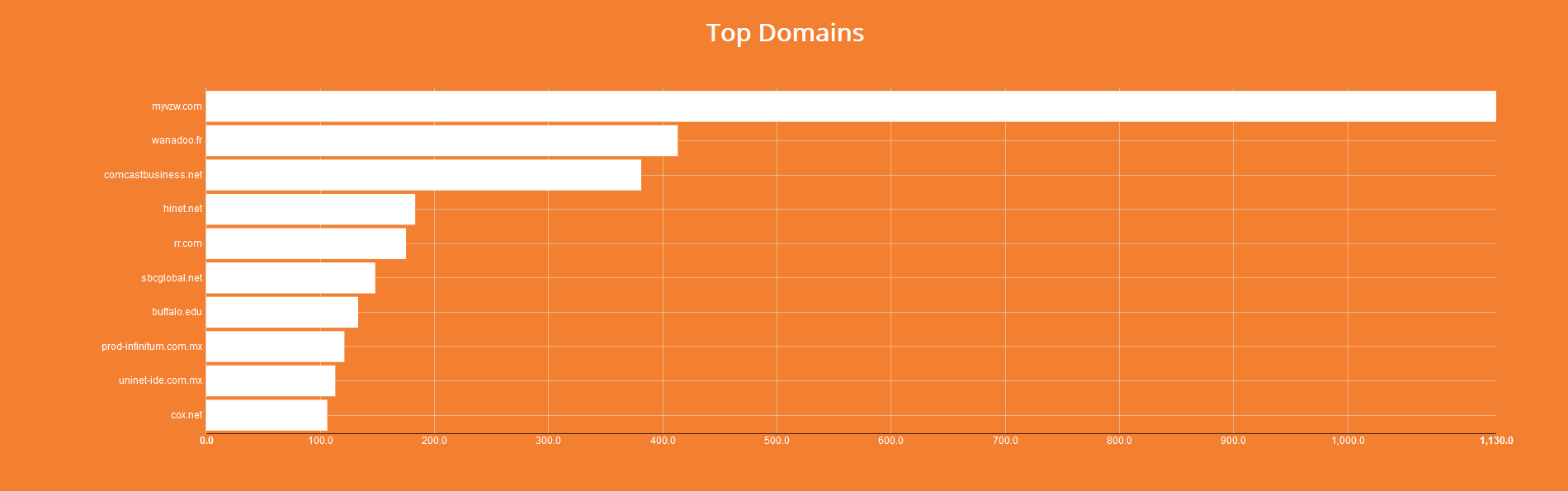
Each of them reports the top five; for example, the first one shows the top five countries having the major number of devices of that type. On the right side, each result is reported with the corresponding device IP address (which I have partially blacked out for privacy reasons) and the body text area which represents device response. By clicking on a device a new page opens up with more detailed informations, including a map showing the geolocation using Mapbox API (omitted in the next image).
Moreover, it is possible to generate reports by clicking on “Create Report”:
The other important feature is represented by filters; they are really useful to improve the search, just like we saw for Google advanced search operators. Some of them are reported next:
- country - filters by two letters country code (e.g. US, JP, FR, IT, RU);
- city - filters by city name;
- hostname - filters by hostname or domain;
- net - filters by IP range (CIDR notation);
- product - filters by technology (es. MySQL, Apache, IIS, Nginx);
- os - filters by operating system;
- port - filters by specific port;
- org - filters by organization;
- geo - filters by geographic coordinates;
- after/before - filters by date (format dd/mm/yyyy and dd-mm-yy).
The application of filters can be done by clicking on the items on the left contained in the top five groups seen before or manually in the search form by specifying the query in this way (example search for SSH port):
port:22
Remember that making a search without filters, it is equivalent to tell to the engine to look for the requested information in the body text area.
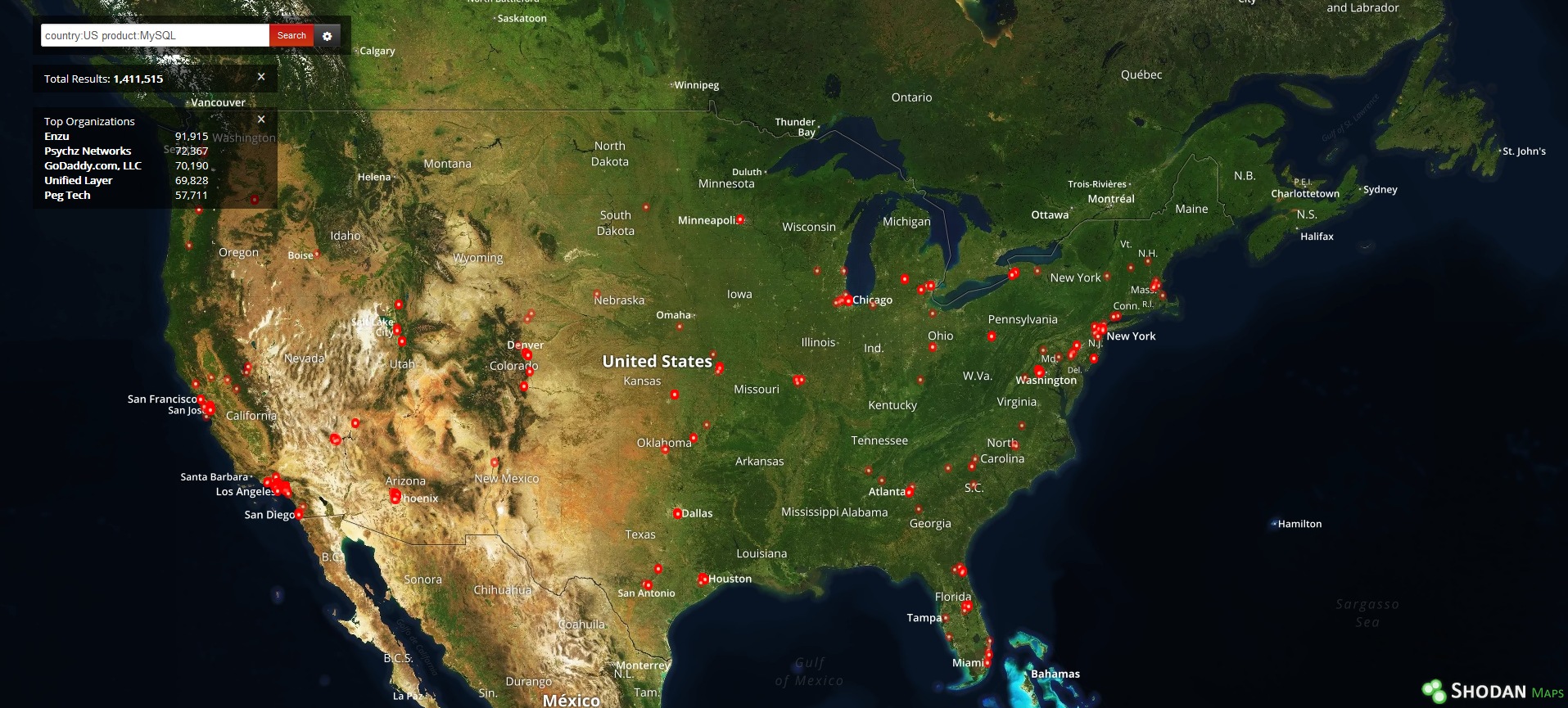
If we want to find all MySQL servers in USA, the query will be:
product:"MySQL" country:"US"
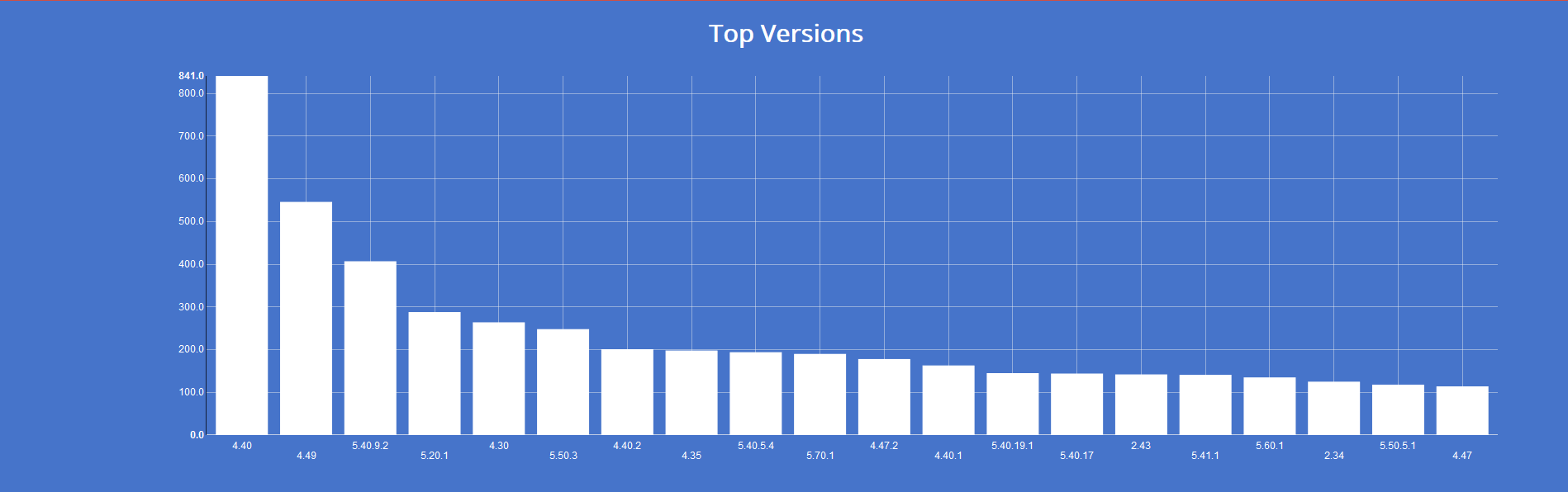
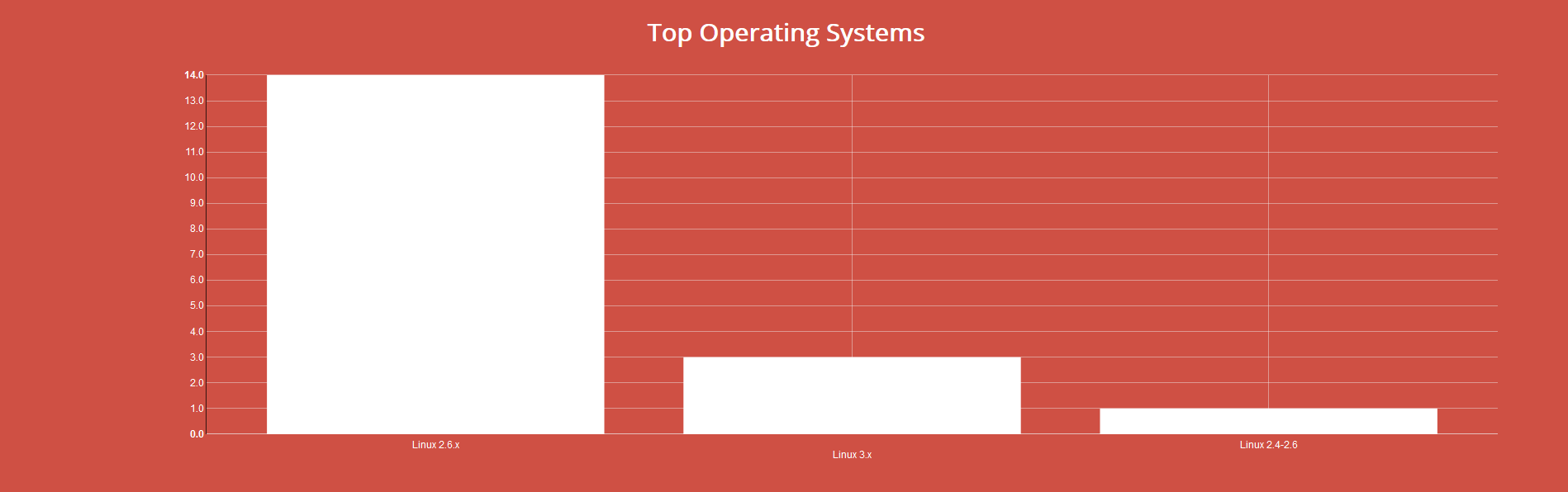
On the left side of the results page we get two interesting groups: top operating systems and top versions.
They can be used to apply other two filters; for example, we can choose to search for old Windows XP operating systems (!) and then 5.1.71-community version of MySQL (this version appears on the left after filtering by O.S.):
country:"US" product:"MySQL" os:"Windows XP" version:"5.1.71-community"
There is also an interesting application, available at https://maps.shodan.io, through which we can even look at a map with pinpoints indicating the geolocation of devices, in this case public MySQL servers in USA:
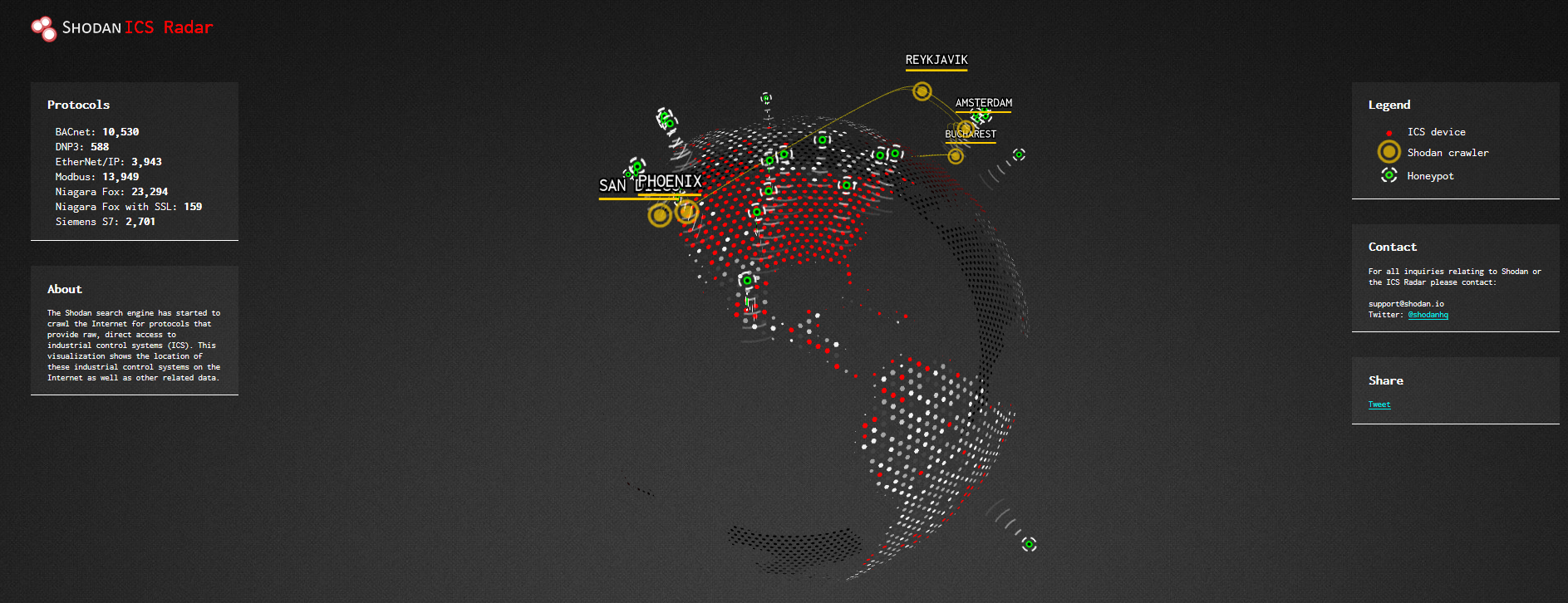
In terms of Industrial Control Systems (ICS), Shodan has also a pretty nice informative animated graph called Shodan ICS Radar showing a worldwide display of ICS accessible via web:
I suggest to experiment with filters of all types to get familiar with queries and take advantage of the full potential of this search engine. Shodan can be a very useful tool to verify if a company network has critical nodes publicly exposed or not properly configured.
Bonus query:
has_screenshot:true